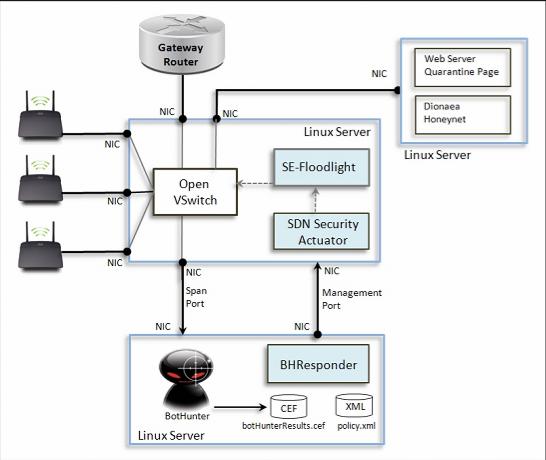
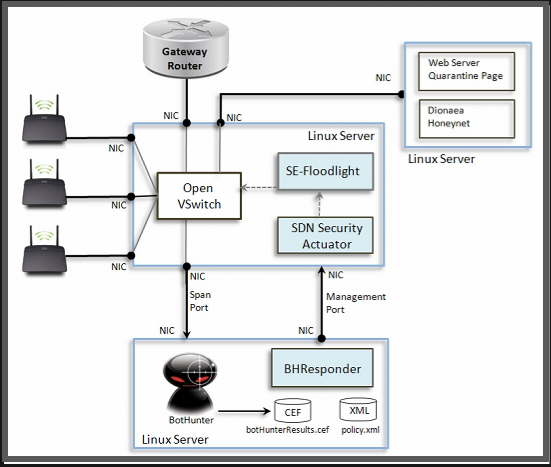
This 3-server network configuration serves as our first Beta test deployment and reference deployment of an SDN-enabled self-defednding wireless network. Using this configuration, OF-BotHunter implements dynamic quarantine, honeynet redirection, dynamic blocking of attack sources and botnet command and control servers, and spam and SSH scan supression.
On the center server, we deployed Open VSwitch, v1.11. It operates as a switch for three WiFi access points, provides a span port to the OF-BotHunter server, a connection to the quarantine notification server and honeynet, and a connection to an Internet gateway router. We use SE-Floodlight as the OpenFlow controller, and we can interchangably use the Java or Perl SDN Security Actuator to implement the security response directives produced by OF-BotHunter.
The OF-BotHunter server (bottom box) uses BotHunter v1.72 an BHResponder Beta 1. BotHunter continually monitors all assets that use this WiFi for indications of malware infection. When an infection is detected, BotHunter communicates the infection profile the BHResponder via the botHunterResults.cef (Common Event Format) event log. BHResponder matches each infection profile against the set of its threat response policies and send security directives to the SDN Security Actuator as defined by the matching policies. BHResponder communicates the the SDN Actuator over SSL-tunnel.
The Counter Intelligence server (upper right) operates a web server hosting the infection quarantine notification page, a DNS server that logs and redirects all DND queries from infected hosts, and a Dionaea honeynet.